Have you heard about session recordings many times? If your answer was “yes”, it’s not just a coincidence. Website session recordings have become an essential part of website analytics. Most big companies use this technique to gather data from their customers and to understand and address any problems customers may encounter.
Do you fully understand session recordings? Do you grasp all its benefits, the plug-in mechanism, or how this tool manages customers’ personal information? Understanding these aspects is crucial to avoid wasting money.
In this article, we’ll delve into one of these aspects. Protecting personal information is crucial, especially with online EU regulations in place. Nobody wants to share credit card information with strangers, and nobody wants companies to trade their personal information for profit. Data masking is an effective solution to this problem. The next section will introduce its mechanism and how effective it really is.
Table of Contents
What is data masking?
As we already mentioned, data masking is a way to protect personal information. The definition is the following: This technique substitutes the original data with false, randomized data with some shuffling or data manipulation techniques. However, data masking ensures that the key figures still stay the same, so different programs can still reach the same conclusion as they would reach with the original data set.
Data masking techniques
There are plenty of different data masking techniques, just as:
Scrambling
This technique randomly replaces numbers and characters, with different numbers and characters. The problem with this technique is it can only replace a number, with another number, a letter with another letter, and so on. Therefore easy to track.
Nullifying
This technique adds null values to columns which really make data stealers work difficult. The problem is, many times your analytics tools can not interpret the values as well.
Substitution
This technique replaces the original value with another value. Since in this case, a numerical value can evolve into letters or symbols, it is very hard to decode. Basically, this is the most used technique.
There are some other useful techniques across the world of data masking, however, you don’t need to learn all of its possible occurrences. These examples showed you the whole mechanism behind this secure data protector solution, and that’s enough for now. Instead of introducing more types of data masking techniques, let’s meet their relevance and usefulness.
What data masking can be used for?
In a shorter version data masking is good for accepting all the online privacy regulations and still gaining some data from the customers. However, it is a little more complicated than that.
This chapter will introduce the possible usage of data masking with all of its available opportunities.
1. Saving your stored data from data breach
First, we should determine what is a data breach exactly. Data breach means that an unauthorized person gets access to sensitive information directly, or indirectly. This unauthorized person can be one of the company’s colleagues who didn’t get access to examine some data, an outsider criminal whose main purpose is to gather that information or an insider who shares sensitive data with the world to harm the company he has been working for.
The real harm is when this unauthorized person gets access to Personal Identifiable Information, which is usually abbreviated as PII.
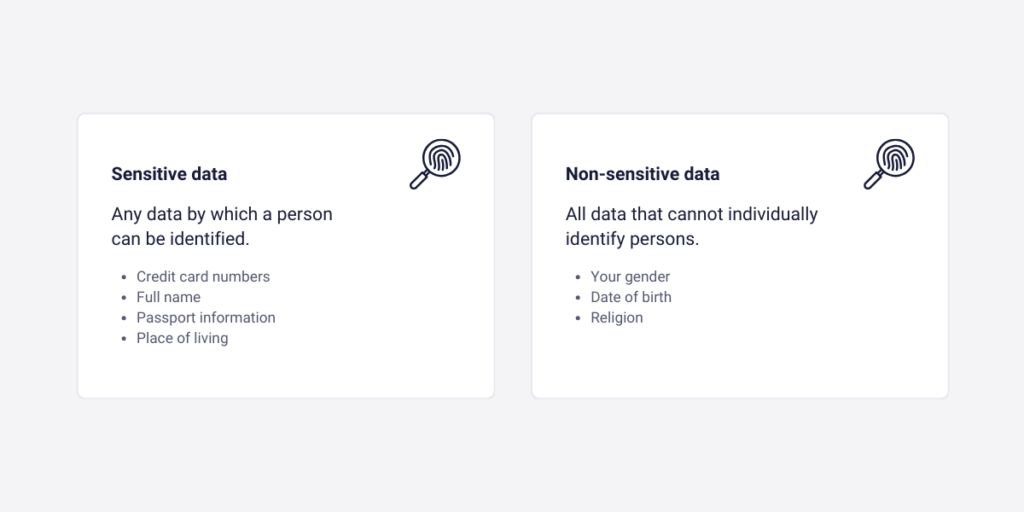
Sensitive data
PII contains all the sensitive data that by just its own, or with other relevant data can identify an individual. There are two types of PII, sensitive and non-sensitive. Sensitive personal identifiable information contains all of the data that can identify a person, even if we know only one of the types of sensitive data.
- Credit card numbers
- Full name
- Passport information
- Place of living
These can all show you who you are thinking of which is unquestionably against the law. You need to somehow data mask this information to hide it securely.
Non-sensitive data
Non-sensitive is another interesting point of this whole topic. These include all the data that can not identify persons single-handedly.
- Your gender
- Date of birth
- Religion
However, and here is the twist, this non-identifiable information can turn into identifiable information very quickly. If we link non-sensitive data to another non-sensitive data it can be mixed as a sensitive one.
Data breaches
But let’s get back to data breaches. What can go wrong if your stored data gets into unauthorized hands? Well, everything. Yahoo, Alibaba, or LinkedIn can all share stories with you. These companies lost most of their reputation due to data breaches, and they spent the next few years building their reputation back with little or average success. Fixing these types of issues definitely causes you financial instability, and there’s a chance that you may hit rock bottom.
⚠️ Don’t forget, implementing proper data masking techniques before storing and analyzing customer data can significantly reduce the risk of facing devastating lawsuits from data breaches linked to your company.
2. To obey the regulations
We already mentioned through the topic of data breaches that in terms of giving out sensitive data you can easily go to court, but we have even darker news. You don’t need to give out sensitive data to get sued. If you don’t hide your customers’ sensitive data appropriately, or if you miss noticing your customers that you will track some of their personal data, you may not just lose the company itself, but your freedom as well.
GPDR (General Data Protection Regulation)
GDPR – or General Data Protection Regulation – defines the difference between personal data and sensitive personal data.
GDPR consists of articles that strictly rule out what companies need to do in different situations. This regulation package contains a lot of nuances, and you can easily find yourself in trouble if you don’t study its articles all around. Sometimes you need to ask your visitors about a possible data recording, sometimes you need to be aware of what types of data you share with your clients.
If you do not obey the mandatory obligations, you won’t only face fines, and court cases, but the immediate losses of your customers. Luckily, as well as in the last case, data masking techniques are here to help you. Although this technique does not help you with obeying all the regulations, it does take the burden off you in some cases.
3. Not letting every colleague get access to the data
When we mentioned data breaches, we had a few words about insiders. Insiders, who work inside the company, but not in the appropriate role to get access to these sensitive data. There are a few tasks when one of the company’s members needs to get access to some sensitive data. Not gathering all in one situation of course, but it is impossible to avoid these tasks from time to time. However, these times it is crucial that only one, or a few members “touch” with these sensitive data, and not the janitor of the company.
💡 A well-optimized data masking can help your company avoid these depressing situations with just a simple trick. Data masking can designate different users who can continuously get access to some parts of the personal data, meanwhile, others can’t.
Although data masking can be the key to protecting your customers and visitors’ personal belongings, sometimes these types of techniques are breakable by well-equipped outsider attacks. That was the purpose of the birth of advanced maskings.
What is advanced masking?
Advanced masking is a special feature found only in Capturly Analytics, one of the most detailed data analytics services online.
Our idea was simple: hide all the information in input fields during session recording analysis, so nobody can see what visitors type during their sessions. With this feature, we don’t just hide the most important information like credit card numbers and passwords, which are banned by GDPR, but also any fields that we don’t think will give you much benefit most of the time.
Capturly Advanced Masking
Nowadays, advanced masking is the standard at Capturly Analytics because of the fast-changing regulations worldwide. It’s hard to keep track of which countries have recently changed their rules.
Let me give you an example of why advanced masking is a good first choice. Imagine you live in Australia and you want to track your visitors’ sessions. You pick an analytics tool that records almost everything by default and you’re happy for a while. But then you realize that you’re responsible for following your country’s online data protection rules, not the company providing the tool. If recording certain data is illegal in your country, you could get in trouble, not the analytics company. So, it’s for your own safety. However, there are times when you might need to record the content of these fields if the law allows it.
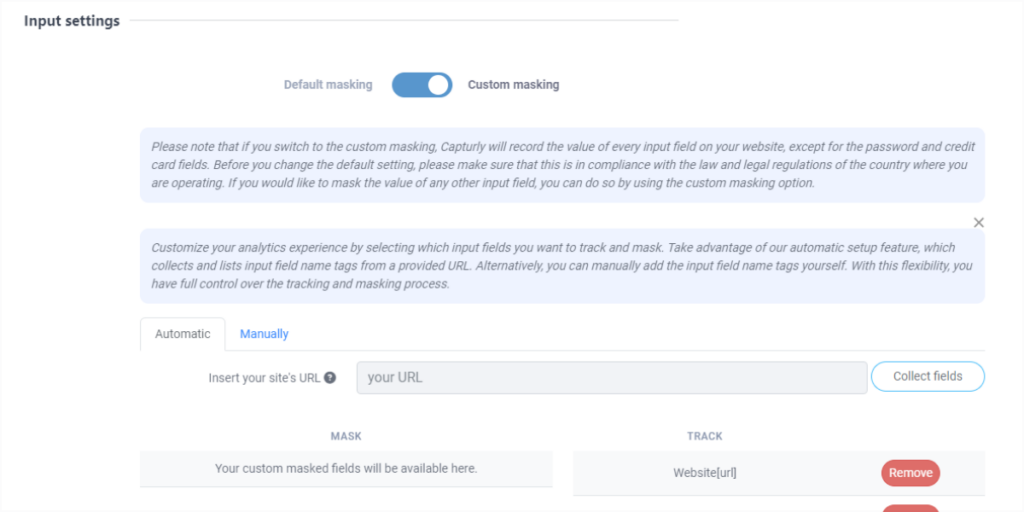
💡 For example, when you need to record interactions with search bars and filters, it’s necessary to turn this feature on. At Capturly, you can easily do this by going to the “settings” menu and switching from default masking to custom masking. This change will automatically allow you to record all the data you couldn’t by default.
In essence, advanced masking is a unique feature in Capturly Analytics that not only protects your visitors from unnecessary data recording but also helps you comply with regional or national online data regulations if you’re unsure of the exact rules.
What does Capturly’s session recording look like?
In this chapter, we’ll talk about our online analytics tool’s session recording feature and all its little opportunities. Specifically, we’ll focus on features that aren’t common in other session recording tools.
💡 For instance, rage clicks are important to track because they help understand why visitors might be frustrated. If an analytics tool can’t track rage clicks, it’s not really top-notch. The same goes for recording technology, location-related filters, or not sampling data (tracking the entire dataset).
But we have some features that aren’t included in most analytics plans or in any of them. Advanced masking, for example, is a great way to protect sensitive data and earn your customers’ trust. It’s rare to find this feature in other website analytics tools, even though data protection is important to them. They usually address this issue differently.
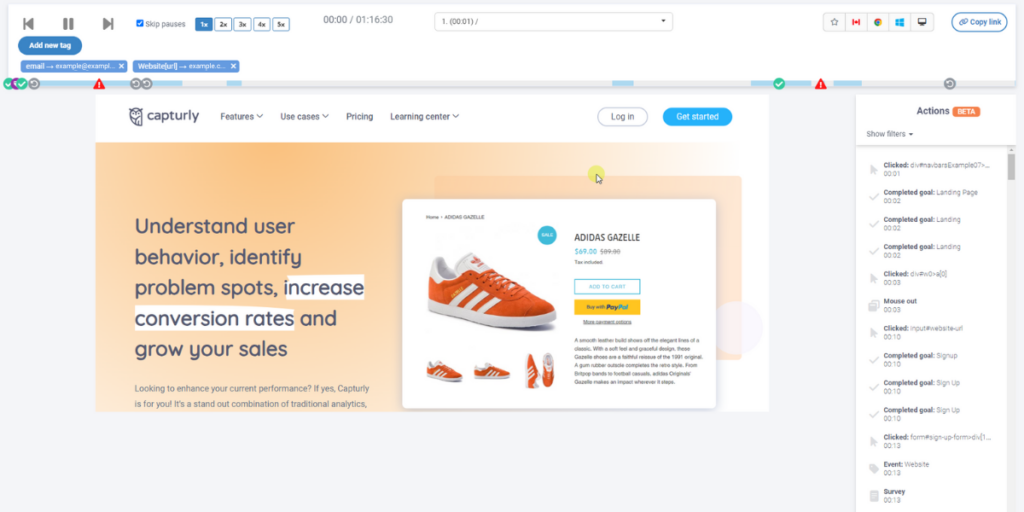
Now, let’s look at those features we haven’t mentioned yet!
The connection between surveys and session recordings
Capturly’s session recording tool is one of the best in terms of synchronization. If a customer completes a survey, you can watch its in-depth analysis in the session recording bar.
When is it useful? Consider an example when 30% of your visitors are not satisfied with your site according to your customers’ completed surveys. You don’t understand this ratio, so you rewatch those sessions, because you are curious who clicked the “not satisfied” button.
After a few hours of watching these sessions, you realize that they couldn’t move to the purchase phase of your site due to a bug. After you fix the bug, the next questionnaire doesn’t bring these kinds of depressive results. However, if the survey function would work individually with the session recording tool, tracking these problems, and finding the real causes takes a lot of time.
The connection between funnels and session recordings
But Capturly Analytics’s software not only synchronizes surveys and session recordings but funnels and session recordings as well. The conversion funnel function can show you how your visitors are converted at your determined goals. If one of your goals is to convince your potential buyers to click the buy “now button” and 30 visitors click on it from 100 total visitors, your conversion rate in terms of this designated goal is 30%.
Different goals and industries usually come with different average percentages, but that’s not a big, dangerous deal. However, if you consider one of your conversion percentages low, you need to focus on quick improvements. Here, this connection between these two data analytics tools can help you find the “why”-s immediately. Learn: individual session recordings always reveal the hidden obstacles.
The detection of JavaScript errors
Another great function of Capturly’s session recording is the detection of JavaScript errors. Although this function tends to appear in the recent updates of other data analytics tools, our in-depth JavaScript detection is a little bit more than these.
JavaScript is a programming language used by millions of companies in the online world due to its simplicity, and easy-to-use system. However, as with everybody, your coding team can make mistakes, and sometimes, instead of you and your team, your users track them.
Capturly’s JavaScript error tracker system shows you if one of your customer’s sessions contains a JavaScript error, even if the customer doesn’t realize it, since it’s hidden. Our tool can distinguish 6 different JavaScript errors, so you have the option to not only just detect your programming issues, but find solutions in a matter of time.
If you want to learn more about the different JavaScript errors, check our documentation about this exact topic!
Conclusion
In this article, if you took good notes, you learned a lot about important aspects of online data protection and explored the potential threats faced by online data analytics.
Understanding data masking, the best way to protect your visitors’ data online, might seem tricky at first. What are the risks if you don’t use this protection? How does it work, and how can you be sure your visitors’ data is safe after using it? This article provides some answers to these questions!
Additionally, we discussed advanced masking, a key feature of Capturly Analytics for data protection. With this feature, you can’t automatically record the content of input fields on your web pages, which helps you avoid illegal activities and trouble. After covering this topic, we talked about some unique session recording features only found in Capturly Analytics or a few other online analytics companies.
We hope you’ve gathered important information and will benefit your visitors by understanding session recording tools, data masking, and advanced masking. Finally, let’s address some common questions about this topic and provide short answers!
Don't forget, sharing is caring! :)

